Describe the Use of Captive Portals
The captive portal technique makes the user with a Web browser HTTP client to see a special Web page before being granted normal Internet access. What is one valid statement regarding captive portals.

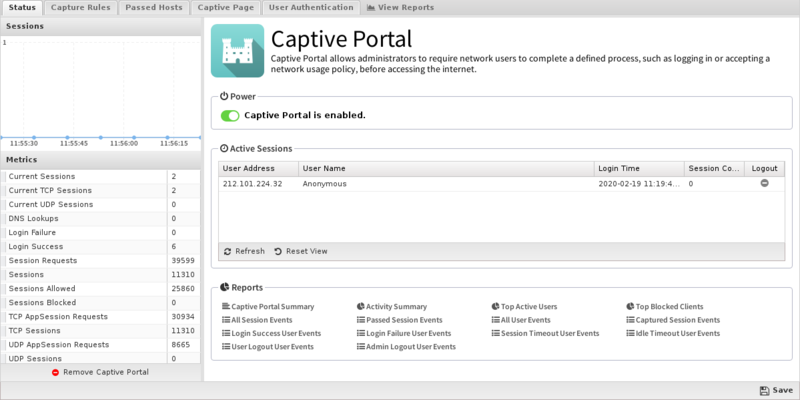
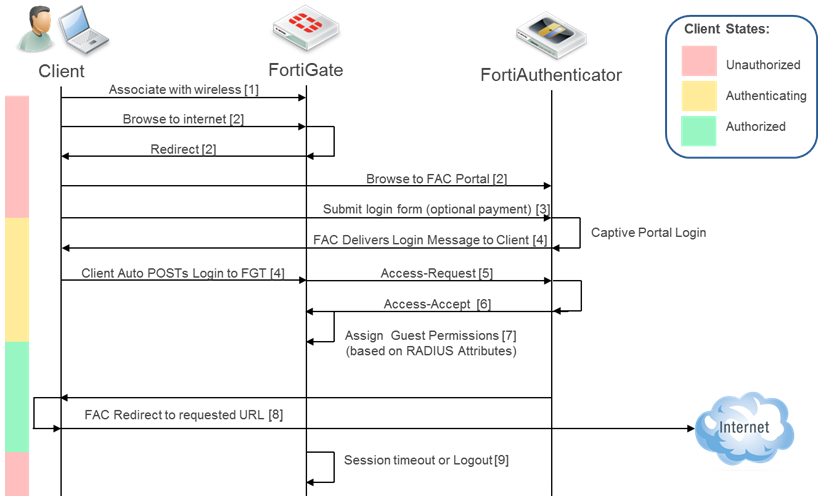
About Captive Portal Authentication
HTTPS is meant to prevent traffic interception alteration and impersonation by a third party.
. The login screen forces guest users to accept the corporate legal disclaimer. That is displayed to newly connected users of a Wi-Fi or wired network before they are granted broader access to network resources. Describe the bug.
The captive portal web-page usually displays the privacy policy andor the terms-of-service TOS document along with some advertisements and sometimes an option to select their preferred language for viewing the portal content and a social login or. But captive portals work by doing exactly that. In fact the dedicated Internet Engineering Task Force IETF CAPPORT working group has now closed because its work has been completed with the ratification of the CAPPORT API RFC7710 and RFC8952 the new captive portal standards.
Hotels RV Parks and numerous other public WiFi providers use captive portals to improve security and ensure that only validated guests use the network. Used at public venues restaurants malls or other space. The captive portal intercepts all packets regardless of address or port until the browser is used as a form of authentication device.
Prepare the Controller for Captive Portal. Apple TV cant connect to captive networks which are networks that require an additional or secondary login. It requires some sort of interaction before granting access to network resources.
After logging in the guest users are provided with a gateway to the Internet. One use for a captive portal is to allow a user to agree to specific terms and conditions in order to access network resources. Captive portal is a redirect page for a companies guest network.
The issue of security of sensitive information transactions is a concern for the captive portal network especially in the authentication process via wireless. Most hotspots implement customer interaction by using a captive portal which is a restricted network connection in which all client HTTP requests are redirected to the providers web site. When the user connect a public wifi Hot-Spot with a Captive portal login page what password protected then programs can not connect to the internet.
And using UDP port 53 DNS programs can connect to the internet. Every time you connect to a private network may it be your college office school etc. It was using a captive portal to access and the Apple TV has no method of logging into these types of network configurations.
Captive portal is most often used for guest access access to open systems such as public hot spots or as a way to connect to a VPN. 23 Jul 2021 by Nishanth Bharadwaj. Also referred to simply as the Session a Captive Portal Session is the association for a particular User Equipment instance that starts when it interacts with the Captive Portal and gains open access to the network and ends when the User Equipment moves back into the original captive state.
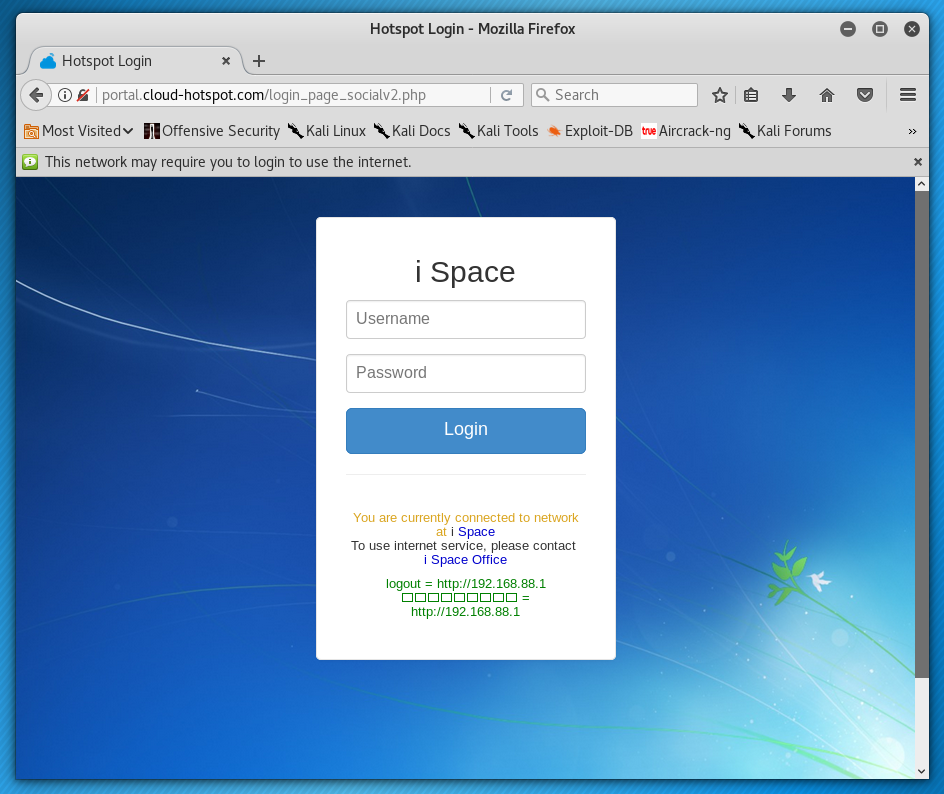
A captive portal is a web page that is displayed to newly connected users of a WiFi network. Keep this always in mind as this will explain most of the issues. This action could be to log in using a username and password or just to accept the networks terms and conditions.
Questions at Issue a. In other words if you want to connect to a network that runs. This program use UDP protocoll to connect to the internet.
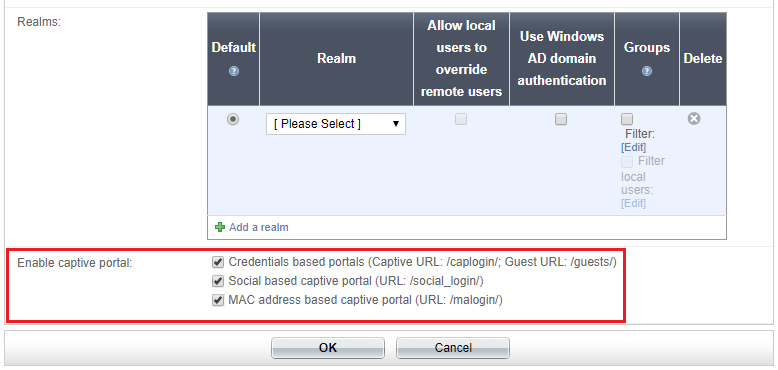
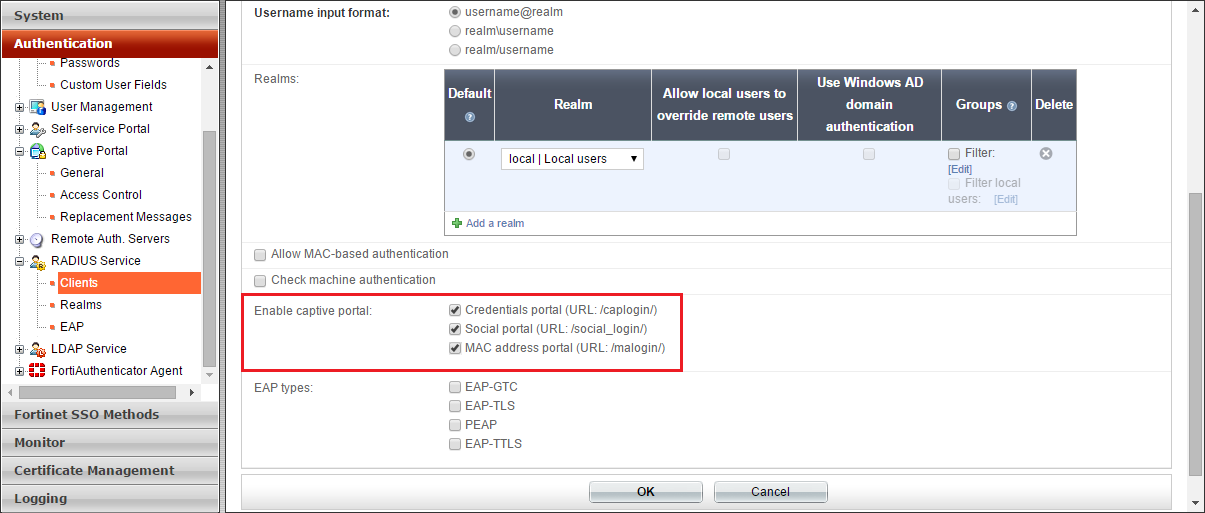
It serves two purposes. Captive portals are commonly used to present a landing or log-in page which may require authentication payment acceptance of an end-user license agreement acceptable use policy survey completion or other valid credentials that both the. This new captive portal API gives Wi-Fi access points a reliable way to advertise themselves as captive portals making it easier for users to.
The web site can then prompt users to agree to the operators terms and conditions enter payment information or enter credentials to verify prior payment arrangements. WiFiRanger routers have been designed to easily deal with such situations. Which of the following describe the two main parts of a computer network security policy.
They are a consistent and easy method of getting consent from visitors to gather information as well as helping to build intelligence on potential customers. A captive portal is basically a system that holds a unauthenticated user captive until some sort of web based authentication mechanism authenticates the user and in this paper we will describe how a captive portal works and how it can be circumvented with fairly easy means. You can use captive portal for guest and registered users at the same time.
Captive portals are commonly used in open access networks available in stores malls clinics airports supermarkets and corporate networks for visitor access management. Authenticate the users is to use a captive portal. It collects web traffic HTTP cookies WebStorage fingerprints browsing profiles page source code privacy policy and screen shots of rendered pages used to verify the data collection process.
The captive portal screen appears where you have to enter your credentials provided by the organization. Captive portals are to blame for a number of security issues especially when it comes to HTTPS websites. A captive portal is what we call a network that requires your action before it allows you to connect to the Internet.
They intercept and alter the connection between the user and the site they are trying to visit. Theres even an Apple Support article I found which states. The captive portal on the Unified controller works like a L2 firewall blocking all traffic on the interface on which the portal is bind on.
The captive portal mechanism implements authentication through the web page or application layer and not through the layer 2 layer. Captive portals are a web page that requires a user action to authenticate before they can access the internet. Selenium is used to visit the hotspot captive portal and perform a wide range of measurements.
The default captive portal web page provided with ArubaOS displays login prompts for both registered users and guests. In captive portal networks users first go through a captive portal session before getting internet access. The idea is to automate that process so that whenever we are connected to any router in the same network it automatically gets logged in.
As the WiFiRanger connects to such WiFi systems the onscreen control panel will alert the user that a login page has been detected providing a. The captive portal allows administrators to provide access to the internet by passing on information that allows user identification such as name e-mail Social Security number or authentication by. Choose two General policy Functional policy.

Linksys Official Support Linksys Cloud Manager 2 0 Captive Portal Guide
Fast And Simple Method To Bypass Captive Portal Hotspot With Authorization On The Web Interface Ethical Hacking And Penetration Testing

Hotspot Using Captive Portal Zeroshell Linux Router

Captive Portal An Overview Sciencedirect Topics
Linksys Official Support Configuring Captive Portal On The Linksys Lapac1750pro Ac1750 Pro Dual Band Access Point

Handbook Fortigate Fortios 6 0 0 Fortinet Documentation Library

A Common Starbucks Captive Portal With An Injected Malicious Script Download Scientific Diagram

New Video How Guest Wifi Captive Portals Work

Captive Portal For Wifi Hotspots Mr96

Linksys Official Support Linksys Cloud Manager 2 0 Captive Portal Guide

All About Captive Portals The Complete And Comprehensive Guide

Captive Portal Api Support Android Developers



Comments
Post a Comment